Welcome Back 2025!
JAYCOR Welcomes You Back in 2025!
Wishing You and Your Company a Prosperous New Year!
JAYCOR specializes in enterprise IT, Industrial OT, and broadcast connectivity solutions across Africa. We are dedicated to delivering mission-critical signal and energy transmission and infrastructure solutions for industrial, enterprise, and broadcast markets. Operates through three business platforms that deliver innovative connectivity solutions: CORE Distribution, Enterprise Projects, and Enterprise Software. Our offering includes:


- Best-in-class cable and connector infrastructure for industrial, enterprise, and broadcast applications, featuring key international brands such as Belden and LEMO®
- Industrial and enterprise switches, media converters, gateways, and active signal transmission equipment, including Belden’s Hirschmann range of switches
- Structured cabling systems for reliable and scalable network infrastructure. Racks, enclosures, tooling, environmental monitoring systems, UPS and PDU energy solutions
- Advanced network management and design software solutions streamline the monitoring and control of networks and data centres. They provide intuitive visualization and configuration tools for seamless network management, while offering enhanced scalability and integration capabilities for larger, more complex systems.
- Robust network access control (NAC) software solutions enable real-time monitoring and enforcement of security policies to protect critical infrastructure. Asset management software solutions help create and build digital infrastructure, integrating real-time data from connected devices across the network, allowing you to leverage the data for improved decision-making and operational efficiency.
As your key partner in building connected infrastructure, JAYCOR supports Industry 4.0, IoT, and IIoT deployments across sectors such as mining, energy, oil & gas, broadcast, ICT, cloud, and telecoms. We source products from leading local and global OEMs and collaborate with top system integrators to deliver innovative solutions across the African market.
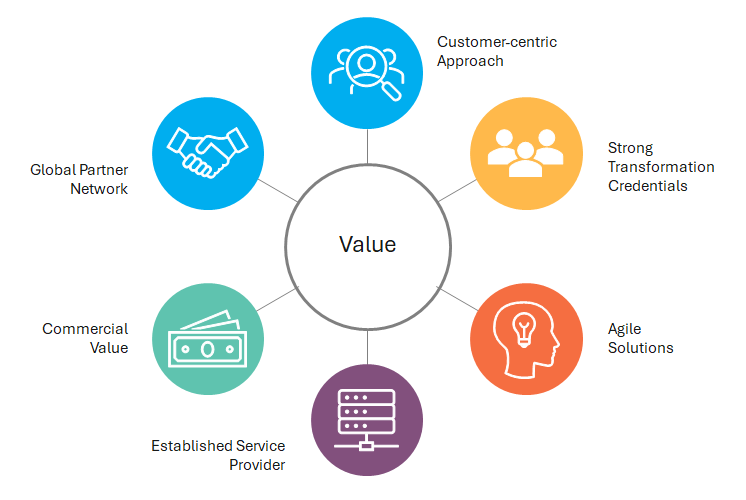
Our Value Proposition Combines Innovation, Inclusivity,
and Exceptional service
 Customer-Centric Approach
Customer-Centric Approach
We prioritize understanding each customer’s unique needs, refining solutions to address pain points, and optimizing their commercial experience.
Agile Solutions
Our vendor-agnostic approach ensures flexibility and rapid responses to market and customer demands.
Global Partner Network
We offer access to over 1,000 OEM brands and $2Bn in inventory through partnerships with F200 distribution businesses across 250 global locations.
Commercial Value
- We deliver financial benefits through preferential payment terms, supplier programs, and rebate incentives.
- Strong Transformation Credentials
- With Black women ownership and leadership, and a diverse management team, JAYCOR drives meaningful transformation.
- Established Service Provider
- Backed by a strong customer base, JAYCOR offers complete supply chain services, and turnkey capabilities.
At JAYCOR, our expertise spans three key verticals to drive innovation and reliability for our clients
- Industrial Sector solutions tailored to the unique needs of industries such as mining, oil & gas, railway signalling and rolling stock, factory automation, materials handling, and industrial networks. Our offerings are built to endure harsh environments, ensuring optimal performance, durability, and safety.
- Enterprise IT, Data centres, and Cloud Infrastructure: From data centres to cloud connectivity, we support digital transformation with dependable, cutting-edge technologies that keep businesses agile, seamlessly connected, and positioned for growth.
- AV Broadcast, Film, and Television: We empower broadcasters in the film and TV industries with high-precision cable infrastructure and solutions, purpose-built to meet the exacting standards and demands of real-time production.

3 Business Platforms Deliver Innovative Connectivity Solutions
- CORE Distribution: The distribution of technology components for connectivity, signal and power transmission systems and networks.
- Enterprise Infrastructure: Building connected infrastructure – turnkey network & data centre infrastructure, ACS/FS, UPS/PDU, cooling and environmental monitoring systems.
- Enterprise Software: Network design, management, real-time monitoring, reporting, asset management, and network access control application solutions and services.
JAYCOR Industrial OT Connectivity Solutions
At JAYCOR, we understand that seamless connectivity is at the heart of every modern industrial operation. Our Industrial Operational Technology (OT) Connectivity Solutions are designed to bridge the gap between industrial equipment and digital networks, ensuring real-time data exchange, enhanced efficiency, and secure operations across your entire ecosystem.

Key Features:
- Comprehensive Cabling Infrastructure: We offer robust cabling solutions designed to handle the demands of industrial environments, ensuring reliable and efficient data transmission for all your OT needs.
- Active Signal Transmission Solutions: Our advanced signal transmission technology ensures that your data is delivered accurately and without loss, even in the most challenging industrial conditions.
- Enhanced Security: Designed with advanced cybersecurity protocols to safeguard your OT infrastructure, keeping your critical systems protected from cyber threats.
- Network Design and Management: From initial design to ongoing network management, our experts ensure your network is optimized for performance, scalability, and resilience. We provide a fully integrated solution to manage traffic, connectivity, and network health.
- Asset Management Applications: Our asset management tools allow you to track and monitor your physical and digital assets, ensuring optimal utilization, maintenance, and lifecycle management across your OT network.
- Real-Time Data Access: With secure, low-latency connectivity, we enable uninterrupted data flow from the factory floor to the cloud, providing you with actionable insights at every level.
- Future-Ready Technology: Leverage the power of next-gen technologies, such as edge computing and IoT, to optimize your industrial processes and drive innovation.
Why Choose JAYCOR?
- Industry Expertise: Decades of experience in industrial automation and connectivity.
- Customized Solutions: We understand that no two operations are the same. Our team works closely with you to provide bespoke solutions that align with your specific needs.
- Reliable Support: Our dedicated team is with you every step of the way, from design and deployment to ongoing maintenance.
Unlock the full potential of your industrial operations with JAYCOR’s OT Connectivity Solutions. Streamline processes, enhance performance, and future-proof your business for tomorrow’s challenges.
Application Suite
Hirschmann Industrial HiVision and ProVize are advanced network management solutions designed to streamline the monitoring and control of industrial Ethernet networks.
HiVision provides intuitive visualization and configuration tools for seamless network management, while ProVize offers enhanced scalability and integration capabilities for larger, more complex systems.
Macmon, from Belden, delivers robust network access control (NAC) solutions, enabling real-time monitoring and enforcement of security policies to protect critical infrastructure.
PatchPro offers DCIM asset management solutions for digital infrastructure, digitizing all assets and managing cabling, connectivity, active network equipment, and rack infrastructure within data centres or switching hubs. integrate real-time data from connected devices across the network, allowing you to leverage the data your business generates for improved decision-making and operational efficiency.

Together, these tools support reliable, secure, and efficient network operations with advanced IoT and IIoT data capabilities.
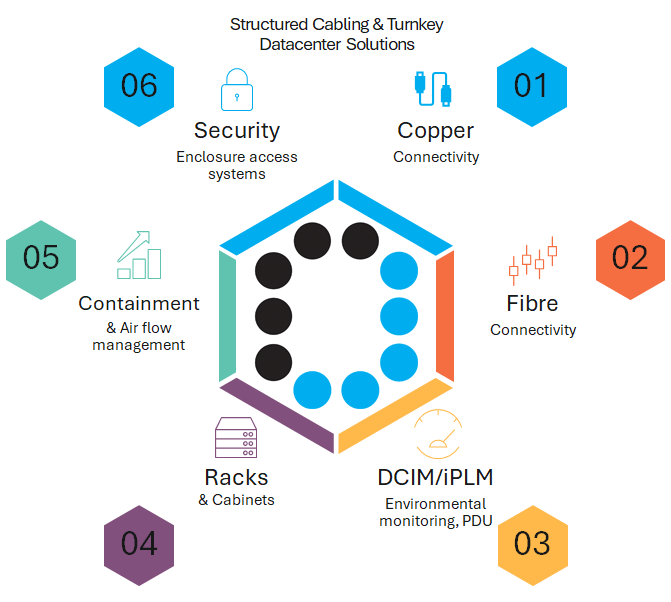
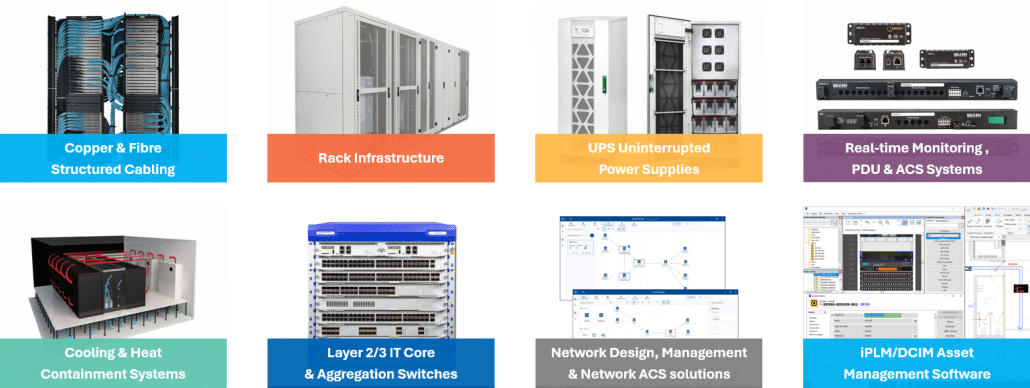
Complete Data Centre Solutions with JAYCOR

At JAYCOR, we provide comprehensive, turnkey solutions for structured cabling, networking, and data centre connectivity. From design to deployment, our expertise ensures seamless integration, robust performance, and scalability to meet modern business needs.
- Optimized Networking: We specialize in robust networking solutions that support complex data requirements, delivering the bandwidth and reliability needed for continuous connectivity.
- Structured Cabling Excellence: JAYCOR’s structured cabling systems form the backbone of your network, enabling seamless integration across all systems and preparing your infrastructure for future needs.
- End-to-End Data Centre Design & Build: JAYCOR’s turnkey approach to data centre construction covers every aspect, from infrastructure planning to final deployment. Our solutions include all critical components needed to ensure a reliable, high-performing data centre environment, such as:
- Racks, Cabinets, and Access Control Systems: Secure and efficient storage solutions for optimized organization and security.
- Cooling, Containment, and Environmental Sensing: Systems to maintain optimal temperatures and airflow while monitoring environmental conditions in real time.
- Uninterrupted Power Supply (UPS) & Power Distribution (PDU) Systems: Reliable power solutions to prevent downtime and ensure uninterrupted operations.
- Real-Time Asset Management and Monitoring with PatchPro® iPLM/DCIM:
Advanced tools for managing assets and monitoring system performance in real time. - Copper and Optical Fibre Cabling and Patching: High-speed connectivity solutions for rapid data transmission.
- DC Fire-Suppression Systems: Advanced fire protection for enhanced data centre safety.
JAYCOR Broadcast Connectivity Solutions: Empowering Your Connection, Enhancing Your Reach
In broadcasting, reliable connectivity is crucial. At JAYCOR, we understand the need for secure, high-speed, and adaptable solutions that seamlessly connect teams and audiences, whether in the studio or on location. Our broadcast connectivity solutions are expertly designed to meet the high standards of the industry, ensuring uninterrupted content delivery even in the most demanding scenarios.
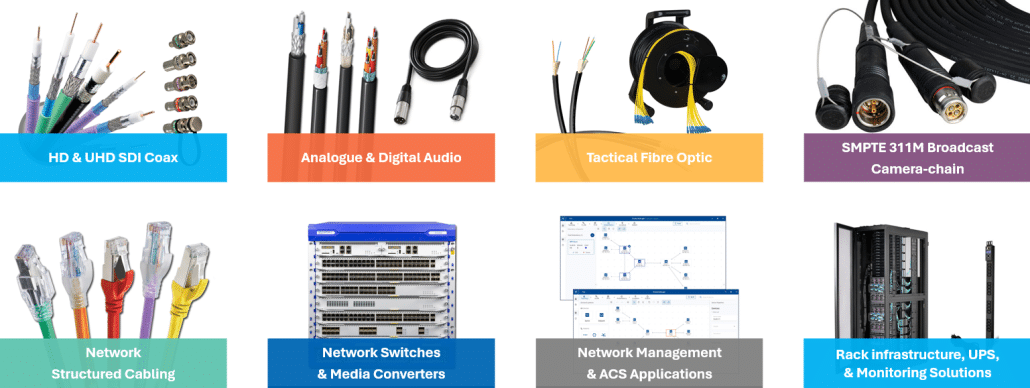
Our Offering:
- Broadcast-Grade Network Infrastructure: High-capacity fiber optics, hybrid cables, and wireless networking systems built to handle data-intensive live video and audio broadcasting with minimal latency and peak reliability.
- Broadcast SDI-HD & 4K Cabling and Connectors: Our specialized cabling and connectors support standard-definition through to 4K quality, providing a clear, dependable signal pathway for high-quality broadcast productions.
- Tactical Fiber and SMPTE 311M Camera Chain Solutions: Purpose-built for outside broadcasting, these solutions are rugged, durable, and optimized for high-stress environments, ensuring robust connectivity even in challenging conditions.
- Active Transmission Components for Signal Broadcasting: High-performance transmission solutions enhance signal quality, reducing degradation and latency to keep your broadcast sharp and in real-time.
- Racks and Infrastructure for Data Signal Housing and Connectivity: Our racks and mounting solutions are designed to keep your data signals organized, accessible, and reliably connected, providing a foundation for efficient signal management and distribution.
- Mobile and Remote Connectivity: From stadiums to remote sites, JAYCOR’s portable and durable connectivity solutions offer quick deployment and resilience under challenging conditions.
- Custom Solutions: Every broadcast has unique requirements. Our team collaborates with you to design bespoke solutions, from system design to on-site support, ensuring you’re ready to broadcast anytime, anywhere.
Why Choose JAYCOR?
With decades of experience in broadcast connectivity, JAYCOR combines technical innovation with a deep understanding of the broadcasting industry. Trust JAYCOR to keep you connected—wherever your broadcast journey leads.
Partner with JAYCOR
Partnering with JAYCOR means gaining access to industry-leading expertise and solutions designed to empower your business:
 JAYCOR stands as a premier provider of connectivity solutions in Africa, specializing in Industrial OT, Enterprise IT, and AV Broadcast. With decades of experience, JAYCOR has established itself as a trusted partner for innovative, high-quality products and services tailored to meet the dynamic demands of modern connectivity. By leveraging cutting-edge technologies, robust infrastructure, and a deep understanding of the African market, JAYCOR ensures seamless integration, exceptional performance, and future-ready solutions for its clients.
JAYCOR stands as a premier provider of connectivity solutions in Africa, specializing in Industrial OT, Enterprise IT, and AV Broadcast. With decades of experience, JAYCOR has established itself as a trusted partner for innovative, high-quality products and services tailored to meet the dynamic demands of modern connectivity. By leveraging cutting-edge technologies, robust infrastructure, and a deep understanding of the African market, JAYCOR ensures seamless integration, exceptional performance, and future-ready solutions for its clients.
The company’s portfolio boasts a comprehensive range of products, from cables and connectivity hardware to fully customized solutions. JAYCOR’s commitment to excellence is underpinned by partnerships with leading global manufacturers, a skilled team of professionals, and a customer-centric approach that prioritizes reliability, scalability, and cost-efficiency.
Partnering with JAYCOR means gaining access to industry-leading expertise and solutions designed to empower your business in Industrial OT, Enterprise IT, and AV Broadcast. With a proven track record, an unwavering focus on quality, and a vision to drive connectivity innovation in Africa, JAYCOR is your ideal choice to stay ahead in a rapidly evolving technological landscape. Let JAYCOR be the cornerstone of your success—connect with us today to build the future of connectivity, together.
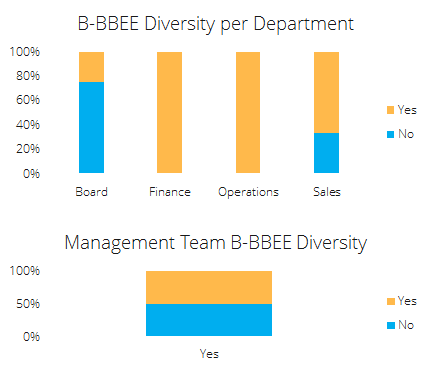
JAYCOR is a strong advocate for fostering a diverse workforce across all departments, management structures, and levels of employee representation.
Greg Pokroy
CEO